Services & Solutions
Using proven data management tools, statistical methods, and software systems, the dedicated team at Frontier Science puts your research on the path to success. Our unique expertise, combined with our flexibility and affordability, ensures the integrity and optimization of your data.
-

Biostatistics
Read more: BiostatisticsOur team of statisticians are well adept to provide an array of statistical services from small, specialized statistical projects up to complete end to end statistical support for all phases of clinical studies.
-

Clinical Trials Data Management
Read more: Clinical Trials Data ManagementWith a comprehensive portfolio of proven data management solutions and a highly skilled team, we can collaborate on studies of all sizes.
-
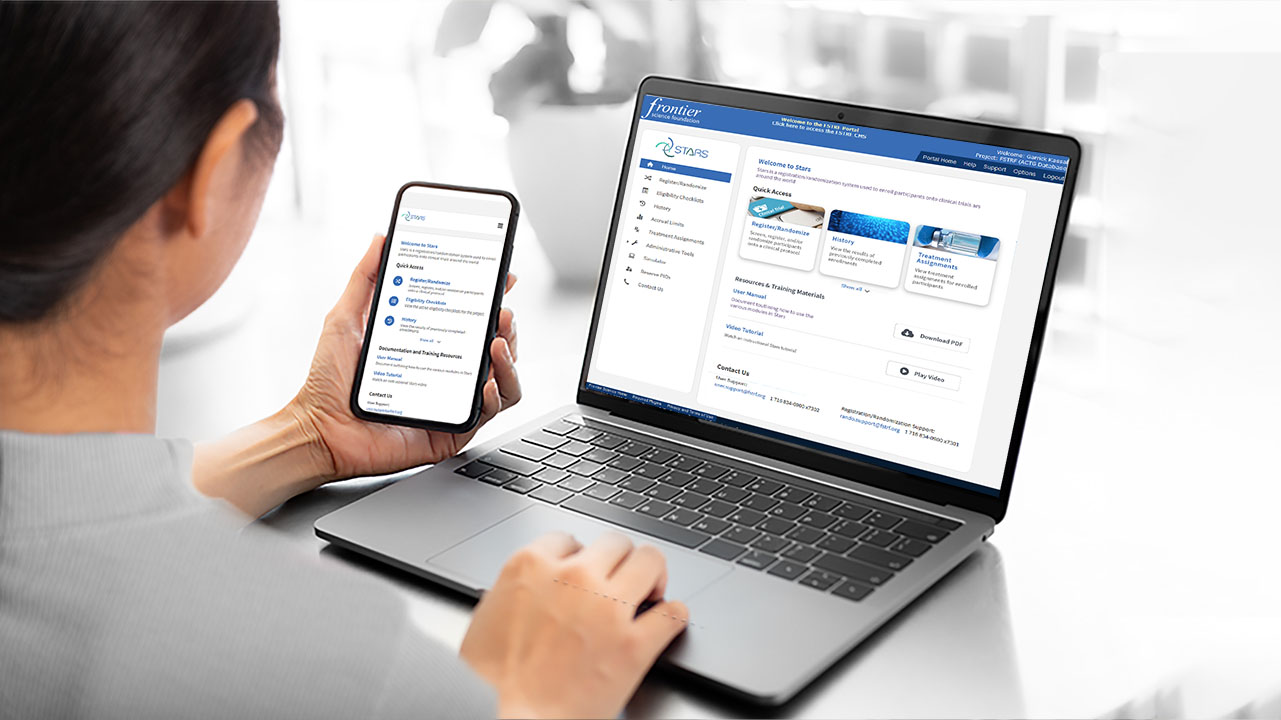
Software Solutions
Read more: Software SolutionsWhether commercial or bespoke, our software engineers are experts in developing and maintaining custom software that comply with industry standards.
-

Monitoring & Auditing
Read more: Monitoring & AuditingOur audit team conducts both remote and on-site monitoring and auditing visits to ensure protocol adherence, participant safety, data integrity, and site readiness.
-

Quality Assurance & Compliance
Read more: Quality Assurance & ComplianceOur integrated quality management systems ensure overall compliance with both domestic and international research regulations.
-

Education & Training
Read more: Education & TrainingOur training specialists curate instructional programs and study documentation tailored to each specific study.